Endpoint Management
დაიცავით თქვენი მოწყობილობები Google Workspace Endpoint Management-ით
Google Workspace Endpoint Management უზრუნველყოფს ყოვლისმომცველ უსაფრთხოებას, რათა დაიცვას თქვენი ორგანიზაციის (ან თანამშრომლის) მონაცემები სხვადასხვა მოწყობილობებზე, მათ შორის Android, iOS და Windows სისტემებზე.
დარწმუნდით, რომ კომპანიის რესურსებზე წვდომა მხოლოდ დაცული და თქვენს პოლიტიკასთან თავსებადი მოწყობილობებიდან ხორციელდება, რაც ამცირებს მონაცემთა გაჟონვის (Data breaches) რისკს.
გაიგეთ მეტი
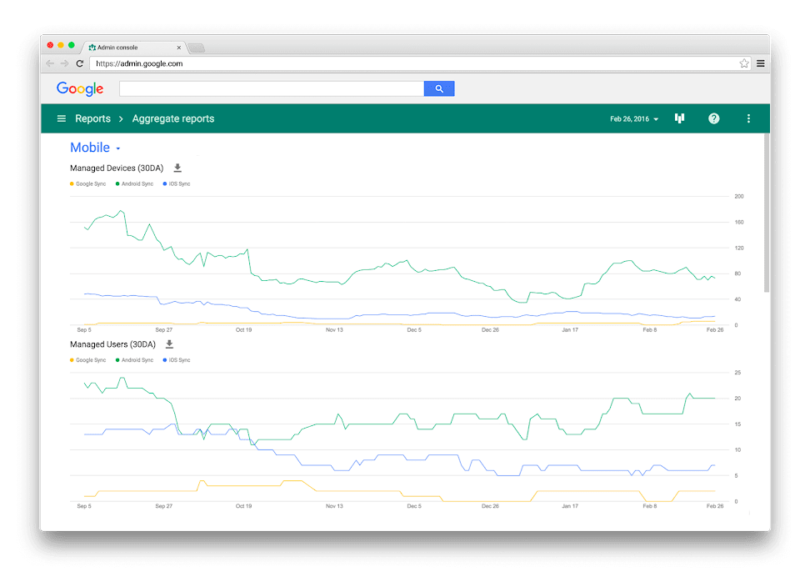
ცენტრალიზებული კონტროლი Android, iOS და Windows მოწყობილობებზე
მართეთ თქვენი ორგანიზაციის ყველა მოწყობილობა ერთიანი პანელიდან Google Workspace Endpoint Management-ის (MDM - Mobile Device Management) საშუალებით. გაამარტივეთ მოწყობილობების რეგისტრაცია (Enrollment), სიტუაციის მონიტორინგი და პარამეტრების მართვა როგორც Android, ასევე iOS და Windows მოწყობილობებისთვის.
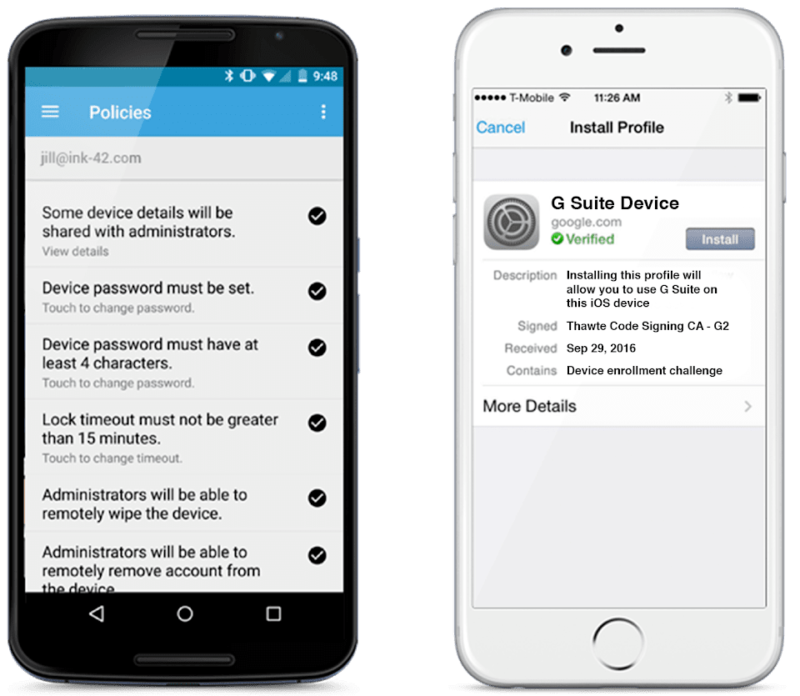
უსაფრთხოების წესებისა და პოლიტიკის აღსრულება
დააწესეთ მკაცრი უსაფრთხოების წესები თქვენს სისტემაში დარეგისტრირებულ (Managed) ყველა მოწყობილობაზე, მათ შორის: პაროლის მოთხოვნები, მონაცემთა სავალდებულო დაშიფრვა (Encryption) და სხვა. Endpoint Management გეხმარებათ შეინარჩუნოთ შესაბამისობა ინდუსტრიის კონფიდენციალურობის სტანდარტებთან.
დაკარგული მოწყობილობების დაბლოკვა და მეხსიერების გაწმენდა
დაიცავით სენსიტიური მონაცემები დაკარგული ან მოპარული მოწყობილობის დისტანციურად დაბლოკვის (Block) ან გასუფთავების (Wipe) მეშვეობით. Google Workspace Endpoint Management გაძლევთ საშუალებას მყისიერად მოახდინოთ რეაგირება უსაფრთხოების ინციდენტებზე.
აპლიკაციების ავტომატური ინსტალაცია და განახლება
მოახდინეთ სამუშაო აპლიკაციების განთავსებისა (Deployment) და განახლების ავტომატიზაცია კომპანიის მოწყობილობებზე. უზრუნველყავით, რომ ყველა მომხმარებელს ჰქონდეს წვდომა პროგრამების უახლეს და დაცულ ვერსიებზე (Patch Management).
MDM ავტომატური რეგისტრაცია
გაამარტივეთ მოწყობილობების რეგისტრაცია ავტომატური კონფიგურაციით, რაც ამცირებს IT პერსონალის დატვირთვას.
კროს-პლატფორმული მხარდაჭერა
მართეთ და აკონტროლეთ Android (Zero-touch), iOS/iPadOS და Windows 10/11 მოწყობილობები.
უსაფრთხოების პოლიტიკა
გააძლიერეთ დაცვის მექანიზმები და მოითხოვეთ ეკრანის ბლოკის კოდები და დისკების დაშიფვრა.
